Microservices Architecture: What It Is and How It Works
At its core, microservices architecture is a design approach for developing software applications as a collection of small, independent services. Each service is focused on a specific business capability and can be created, deployed, and scaled independently from other services in the application.
Consequently, each service typically has its own database and communicates with other services through lightweight APIs—an approach also widely used in Serverless architecture where functions interact via APIs. Developers can build and deploy each service independently, using the programming language and technology stack best suited to its needs. The global microservices architecture market is expected to grow from $6.27 B in 2024 to $15.97 B by 2029 at an 18.8% CAGR.
However, developing, deploying, and managing such a microservices architecture poses its own share of challenges. For a deeper understanding, explore our guide on challenges and solutions in cloud-native application development to see how these issues are addressed in modern cloud-native environments. For instance, managing shared access, ensuring data consistency, maintaining the security of services, facilitating communication between services, and managing dependencies. To address these challenges, design patterns for microservices use architectural patterns that provide efficient administration of these services, overcome challenges, and maximize performance. By choosing the right microservices architecture patterns for your use case, you can increase component reusability and reduce development time and effort. Over time, this can eliminate the need to reinvent the wheel each time you make changes to your application.
Why Microservices Need Design Patterns: Solving Real-World Complexity
While microservice architecture offers significant advantages like independent scalability, modularity, and faster release cycles, real-world implementations often expose underlying complexities that aren't obvious during the initial phases of microservices development.
As organizations begin building microservices or migrating from monoliths, they face architecture-level challenges:
- How should services communicate reliably?
- What happens when a dependent service fails?
- How do you manage transactions across multiple services?
- How do you ensure secure and scalable microservices system design, especially in cloud environments that increasingly rely on Supercloud abstraction with Zero-Trust baked in?
These aren’t just edge cases—they’re everyday realities in microservices-based applications. That’s where microservices design patterns and architecture patterns come in. Organizations adopting microservices reported 63% faster deployment speed , 56% improved agility, and 51% better scalability.
That’s where microservices design patterns and architecture patterns come in.
These are system design patterns and best practices specifically tailored for distributed systems. They help teams streamline microservices implementation by solving critical concerns such as:
- Communication and routing using patterns like API Gateway and Service Discovery
- Resilience and fault tolerance via Circuit Breaker or Retry patterns
- Data consistency with patterns like Saga or CQRS
- Scalability and independence using Database per Service
Without using design patterns for microservices, teams often reinvent solutions, introduce fragility, or face scalability bottlenecks.
By using the right microservices architecture patterns, teams can create a system that is:
- Easier to maintain and evolve
- More resilient and observable
- Better aligned with modern microservice architecture design
Whether you're just starting your journey or planning a monolithic to microservices migration, understanding different design patterns—and the evolution from monolithic to microservices architecture —is key to long-term success.
Top Microservices Design Patterns You Need to Know
While there are several microservices design patterns, we'll discuss some of the most noteworthy and commonly used design patterns here. Find out why they are important and how they are used.
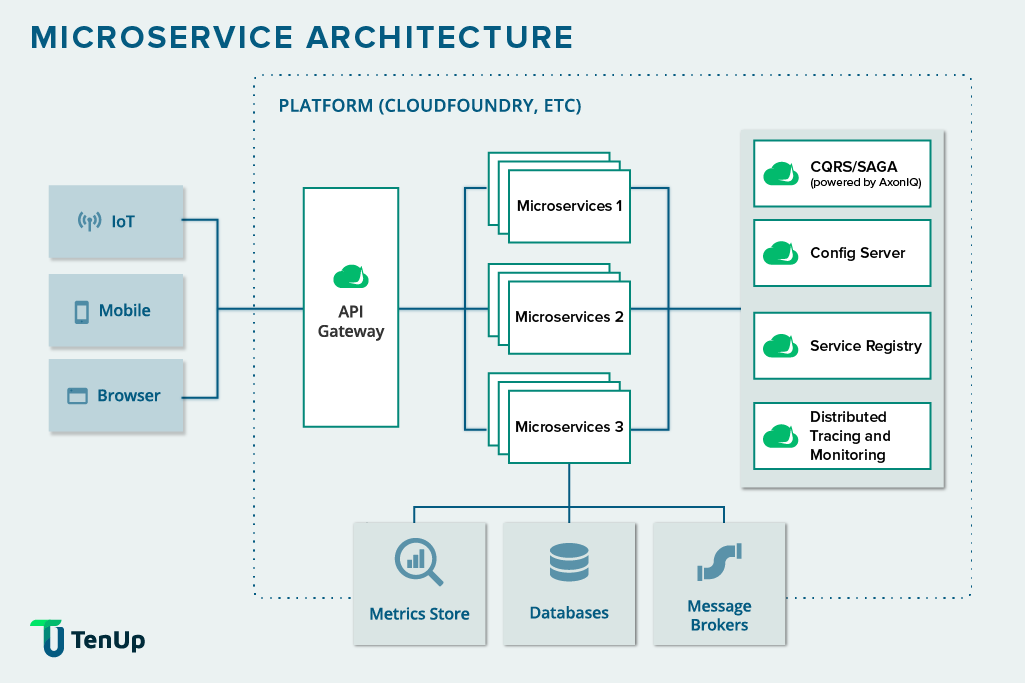
API Gateway: Simplifying Communication in Microservices
As a microservices-based application grows in complexity, the number of endpoints can become unwieldy—just one of the challenges developers face when building scalable cloud-based apps. An API gateway acts as a single entry point to the application, abstracting away the complexity of the underlying microservices.
Why It’s Useful:
- Provides a single endpoint for clients, removing the need to know the specific location of each microservice.
- Handles communication complexity between clients and microservices behind the scenes.
Key Functions:
- Authentication – Ensures only authorized requests pass through.
- Rate Limiting – Controls traffic to prevent overload.
- Request/Response Transformation – Formats data between client and service.
- Service Discovery – Finds and routes to the correct microservice automatically.
Additional Benefits:
- Improves security, scalability, and reliability of microservices architecture.
- Centralizes traffic management and service monitoring for easier operations.
Authentication and Authorization with OAuth2 and OpenID Connect
Modern microservices architectures often adopt token-based authentication standards like OAuth2 and OpenID Connect to secure user access and assign permissions. This approach ensures that every request is verified and authorized before it reaches the intended service.
Use Case Example:
A SaaS platform issues JWT (JSON Web Token) access tokens to authenticated users and validates scopes or claims on each microservice request, ensuring that users only access resources they are permitted to.
Best Practices:
- Centralize identity management with services like Auth0, Okta, or Keycloak.
- Avoid embedding credentials or tokens directly into microservices code.
- Enforce short-lived tokens with refresh capabilities for improved security.
API gateways also provide other important functions, such as authentication, rate limiting, request/response transformation, and service discovery. These features can help improve the security, scalability, and reliability of a microservices architecture.
Another benefit of using an API gateway is that it can simplify the management and monitoring of a microservices architecture. By centralizing the routing and communication between services, an API gateway can provide a single point of control for managing traffic and monitoring service performance.
Using Access Tokens for Secure Microservices Communication
Access tokens are commonly used as a security mechanism in microservice architecture to authorize and authenticate requests between services.
How it works:
- A client sends a request to a service.
- The receiving service verifies the client’s identity by checking the included access token.
- If valid – the request is authorized and processed.
- If invalid or expired – the request is rejected, and an error is returned.
- The service may issue a new access token in the response, allowing the client to use it for future requests.
Token Management:
- Typically generated by an authentication service or identity provider (e.g., Auth0, Okta, Keycloak).
- Contains user/service identity details and a time-to-live (TTL) value for validity duration.
Why It Matters:
- Enhances security by ensuring only authenticated requests are processed.
- Improves scalability and flexibility in distributed systems.
Mutual TLS (mTLS) for Service-to-Service Encryption
For sensitive workloads, mutual TLS provides an additional layer of security by requiring both the client and the server to present valid certificates during the connection handshake. This ensures encrypted communication and mutual trust between internal services.
Use Case Example:
In a financial services application, all internal API calls are encrypted using mTLS to safeguard transactions and protect customer data in transit.
Why It’s Critical:
- Prevents man-in-the-middle attacks.
- Enables end-to-end encryption within the service mesh.
- Commonly integrated with service mesh solutions like Istio or Linkerd.
Access tokens are typically generated by an authentication service or identity provider, which is responsible for verifying the identity of users or services and issuing access tokens. The access token usually contains information about the user or service that it represents, as well as a time-to-live (TTL) value that indicates how long the token is valid.
In addition, to the security benefit, access tokens allow for improved scalability and flexibility in a distributed architecture.
Service Discovery: Ensuring Seamless Interaction Between Services
Service discovery is the automatic detection of devices and services over a network, reducing manual configuration efforts in microservices and containerized environments, often supported by a service mesh for secure microservice communication.
Why It’s Important:
- Microservices are deployed independently and may run on different servers or containers.
- Without service discovery, each service would need a manually configured list of other services — a tedious and error-prone process.
How It Works:
- A service registry acts as a central repository tracking all services, their locations, and metadata.
- When a service needs to communicate with another, it queries the registry to locate it and then establishes a connection.
Popular Tools:
- Consul
- etcd
- ZooKeeper
- Kubernetes (built-in service discovery support)
Benefits:
- Simplifies connectivity between microservices.
- Reduces operational overhead.
- Enables dynamic scaling without manual reconfiguration.
There are different ways to implement service discovery in microservices, but one common approach is to use a service registry. A service registry is a central repository that keeps track of all the services in the system, along with their location and other relevant metadata. When a service needs to communicate with another service, it queries the service registry to find the location of the desired service, and then establishes a connection to it.
Some popular tools for implementing service discovery and service registries in microservices include Consul, etcd, and ZooKeeper. Additionally, some container orchestration platforms, such as Kubernetes, have built-in support for service discovery.
Secure Service Discovery
While service discovery ensures connectivity, securing it is crucial to prevent spoofing or unauthorized service registration.
Use Case Example:
Microservices register themselves with a secure registry such as Consul or Eureka, which validates the identity of each service before accepting registration.
Security Tips:
- Use signed metadata for service registration.
- Combine with firewall rules or identity-based access controls to prevent rogue services from joining the mesh.
Circuit Breaker Pattern: Enhancing Resilience in Microservices
The circuit breaker pattern improves the resilience and fault tolerance of microservices by detecting failures and temporarily halting access to affected services.
How It Works:
- Detects failures in a service or component.
- Temporarily halts requests to prevent cascading failures.
- Resets once the service recovers, allowing requests to resume.
Why It’s Needed in Microservices:
- Network latency, timeouts, or service failures can occur when services communicate over a network.
- Prevents overloading services already experiencing issues.
Benefits:
- Improves reliability and resilience.
- Reduces downtime risk.
- Handles unexpected failures gracefully.
Distributed Tracing: Monitoring and Optimizing Microservices Performance
Distributed tracing provides visibility into the flow of requests between microservices, helping diagnose bottlenecks and errors.
How It Works:
- Instruments requests/responses to create a trace for each interaction.
- A trace includes processing time, involved services, and error details
Core Components:
- Tracer – embedded in each service to record trace data.
- Collector – aggregates trace data from services.
- Visualizer – displays trace data in a human-readable format.
Benefits:
- Improves observability of complex, distributed systems.
- Accelerates root cause analysis.
- Enhances team collaboration by providing detailed insights.
CQRS and SAGA: Managing Scalability and Transactions in Microservices
CQRS and Saga patterns enhance scalability, performance, and transaction management in distributed systems.
CQRS (Command Query Responsibility Segregation):
- Separates write operations (commands) from read operations (queries).
- Write model and read model can be independently optimized.
- Improves scalability by specializing each model for its task.
Saga Pattern:
- Manages long-lived transactions across multiple services.
- Each service handles its own transaction step.
- A coordinator service ensures all steps succeed or compensates for failed steps.
Benefits:
- Prevents partial data updates in multi-service transactions.
- Improves fault tolerance in distributed workflows.
Please read our blog on the importance of CQRS and SAGA in microservices architecture to better understand these microservices design patterns.
Zero Trust Security Model
Zero Trust assumes no service or user is trusted by default, even inside the private network. Every request must be verified and authorized.
Best Practices:
- Implement fine-grained authorization with RBAC (Role-Based Access Control) or ABAC (Attribute-Based Access Control).
- Rotate and store secrets securely with tools like HashiCorp Vault.
- Enforce continuous authentication and validation of service identities.
Why It Matters:
Zero Trust reduces the attack surface and improves compliance, which is increasingly critical in the era of cloud-native microservices vs. cloud-based monoliths.
Decomposition Patterns
To break down the architecture into microservices , organizations must apply strategic decomposition patterns to ensure maintainability and scalability.
Key Types:
- business capability: Organize services around core functions like Orders, Payments, or Inventory.
- By subdomain: Align with Domain-Driven Design principles.
- By transaction: Separate services that can work independently without strong transactional coupling.
Use Case Example:
An eCommerce platform splits into User, Cart, Checkout, and Recommendation services, each developed and deployed independently.
Database per Service Pattern
Each microservice manages its own database, ensuring loose coupling and autonomy.
Use Case Example:
A logistics platform uses separate databases for Shipment, Tracking, and Notification services.
Benefits:
- Reduces data conflicts.
- Allows independent scaling and deployment.
- Eliminates shared database bottlenecks.
Conclusion: Mastering Microservices Design Patterns for Success
Microservices architecture offers a number of benefits for modern application development. However, to leverage its full potential, developers need to identify and deploy relevant design patterns. By using the patterns listed here and others, developers can create microservices-based applications that are easier to develop, maintain, and scale.
Our developers have experience creating microservices architecture for a variety of applications across industries. Please read our case study titled Future-Proofing an Established Marine ERP through Microservice Architecture. We utilize different microservices design patterns to develop highly scalable, flexible, and resilient applications in both Cloud and Non-Cloud (On-premise and Hybrid) environments. Need accelerated development and streamlined maintenance with microservices architecture? Our specialized Product Engineering and Cloud Solutions can help!
Frequently asked questions
What microservices patterns should I use when migrating from a monolith gradually?
Use the Strangler Fig pattern to replace monolith features step-by-step with microservices behind an API gateway. Combine it with Decomposition by subdomain, Service Discovery, Circuit Breaker, and Saga for smooth migration, fault tolerance, and data consistency.
How do I determine the right service granularity in my microservices design?
Start with business capabilities—each service should map to a distinct domain function. Aim for high cohesion within services and loose coupling between them. Consider team ownership, fault tolerance, and deployment independence. Avoid overly fine-grained “nano-services” that increase complexity without real benefits. Evolve service boundaries as your system grows.
Can I use multiple design patterns together in the same service or flow?
Yes, and it’s often essential. Combining microservices patterns—like API Gateway with Circuit Breaker or CQRS with Event Sourcing—helps solve complex, real-world problems efficiently. The key is balance: use patterns that complement each other, avoid over-engineering, and ensure maintainability.
Why use Event Sourcing pattern instead of traditional CRUD in CQRS?
Event Sourcing captures every change as an event, enabling full audit trails, rollback, and reliable CQRS projections. It’s ideal for domains needing traceability, like finance or logistics.
What are the most critical anti‑patterns to avoid in microservices?
Smells like shared databases, synchronous coupling across services, excessive synchronous chatty RPC, god‑services, and improper transaction management (e.g. two‑phase commit) are frequently cited anti‑patterns on Reddit and SO communities.
What security design patterns are emerging for microservices in 2025?
Microservices security focuses on zero-trust architectures with service meshes, pod-level mTLS, fine-grained RBAC via identity providers, API gateway enforcement, and secure service discovery with identity validation, enhancing resilience, traceability, and defense-in-depth.
What metrics or fitness functions should guide microservices pattern evaluation?
In modern microservices QA, you measure resilience (error rate, recovery time), scalability (throughput, latency under load), coupling (service blast radius), and developer velocity. Use metrics as fitness functions to validate whether a pattern (e.g. Circuit Breaker, Bulkhead) improves overall quality or not.